Enterprise requires OpenID Connect (OIDC) for authentication, for example with Identity Providers (IdP) such as Google, Okta, Azure AD and AWS Cognito.
General instructions
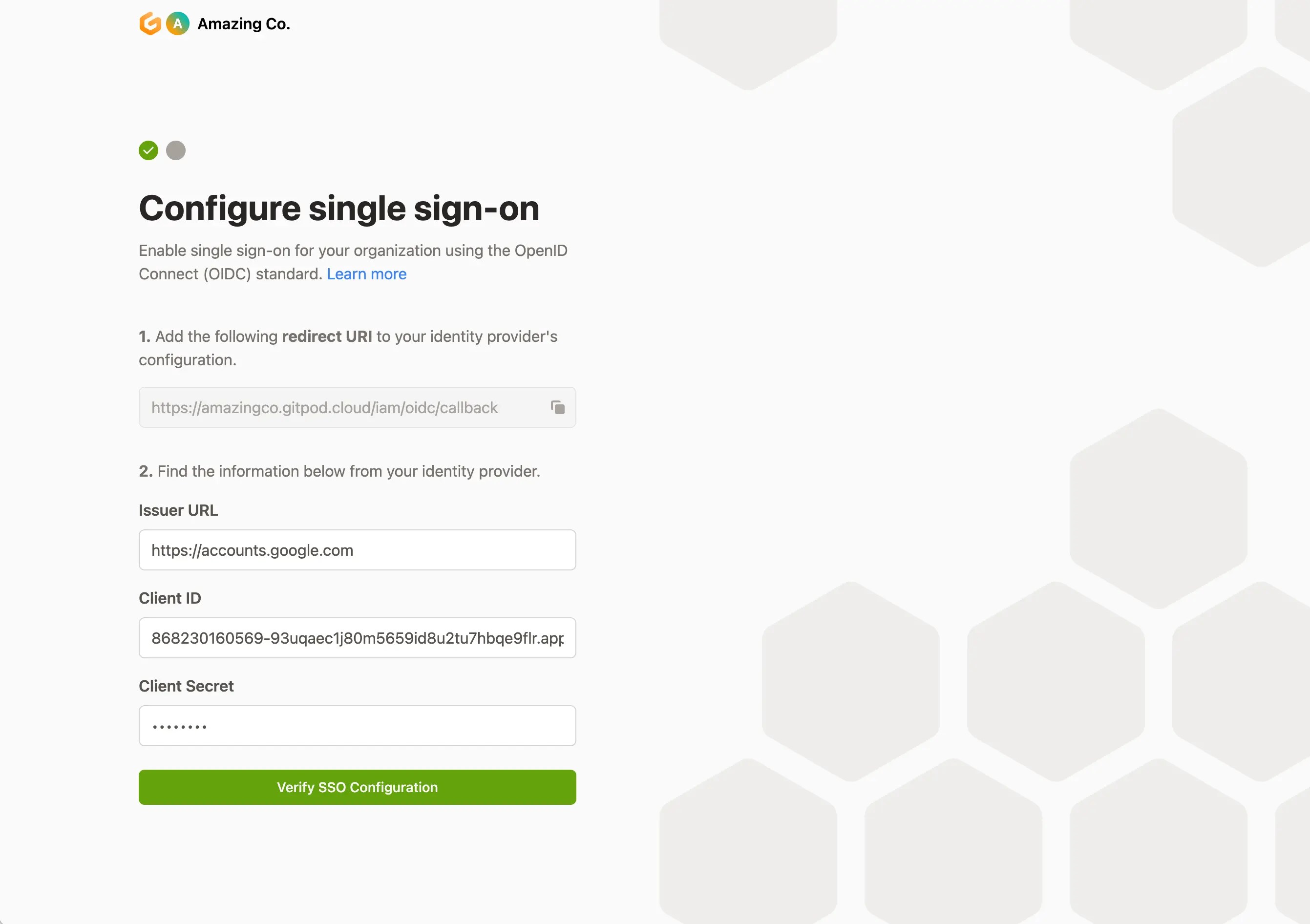
You will need to create a configuration with your Identity Provider and provide the “redirect URI” you can copy from this screen.
Once you’ve created your Identity Provider configuration, you should copy and paste the Issuer URL, Client ID and Client Secret values on this screen.
Clicking “Verify SSO Configuration” will ensure that validity of the values by authenticating your account. If successful, your user will be created and configured with the “owner” role. Subsequent users that log in will be granted the default “member” role.

Identity Provider specific instructions
Let us go through a detailed walk through of how to setup of how to setup SSO in various identity providers:
- Okta
- Azure AD
- AWS Cognito
Okta
As prerequisites, you will need the following:
- Access to your Okta instance
- Permission to create an app integration
Creating a Gitpod SSO Integration
On the Okta Admin dashboard, navigate to Applications
Select
Create App Integration
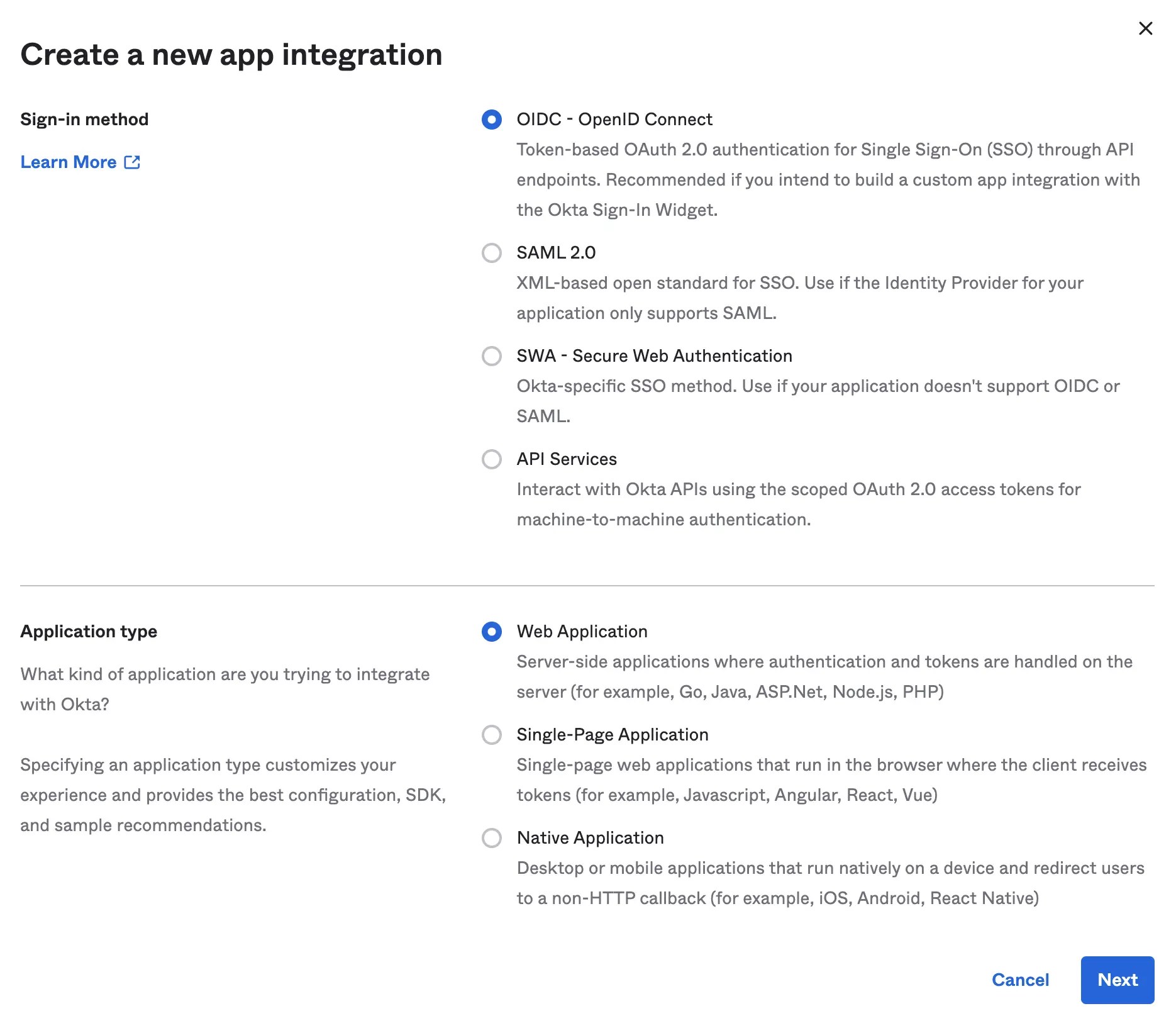
Select the following options and click
NextSee AlsoDiverse Lynx hiring Okta Engineer in Dallas, TX | LinkedInDiverse Lynx hiring OKTA Engineer in Spring, TX | LinkedInBorder0 on LinkedIn: Log in to your Docker containers using your Okta SSO account from anywhere…Identity Should Be Self-Sovereign | Beyond Identity- Sign-in method:
OIDC - Open ID Connect - Application type:
Web Application

- Sign-in method:
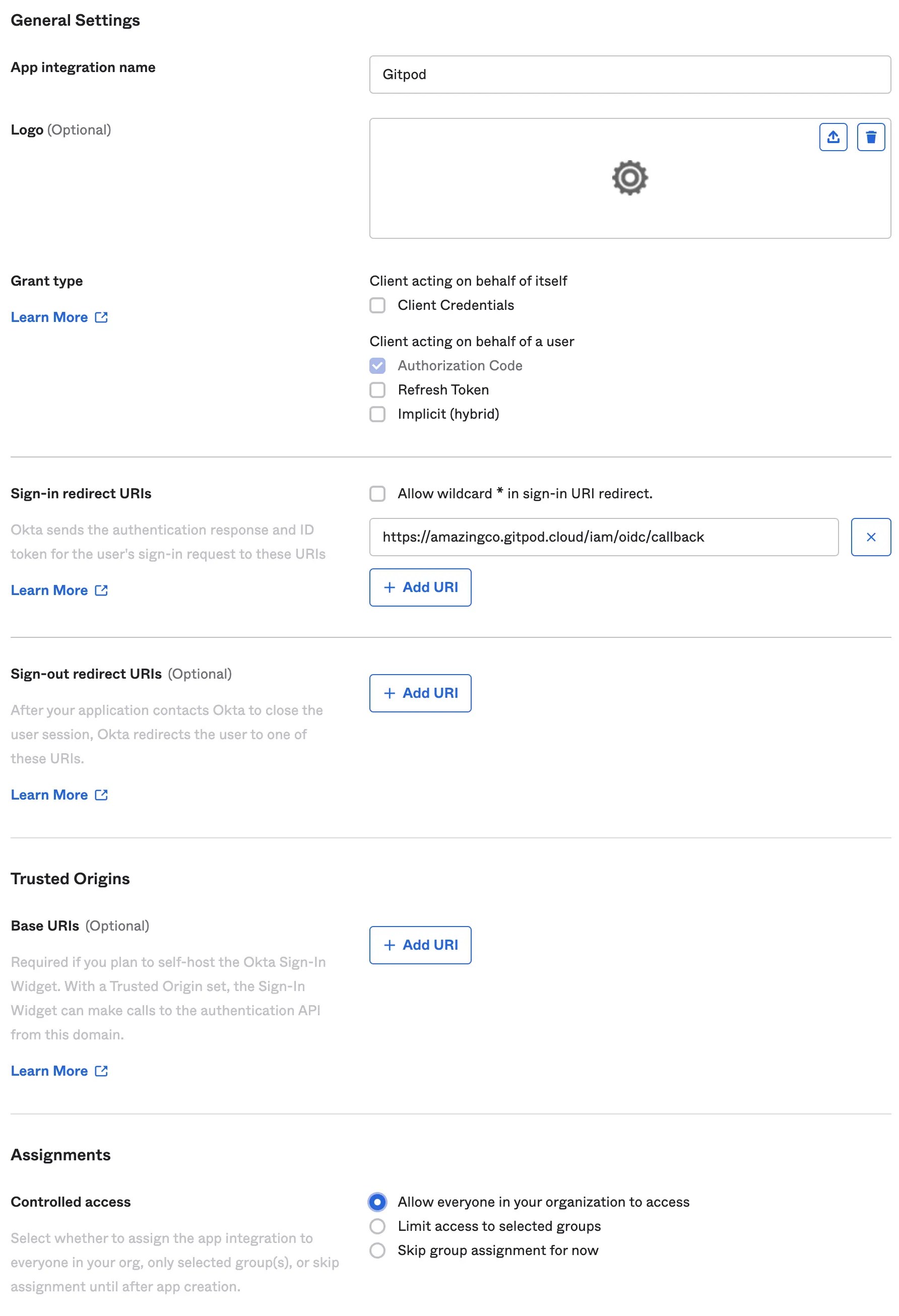
Specify General Settings
- App integration name:
Gitpod(or choose your own name) - Sign-in redirect URIs: copy this value from your Gitpod setup screen (see details above under “General instructions”)
- Sign-out redirect URIs:
none - Trusted Origins:
none - Assignments: choose option appropriate to your organization

- App integration name:
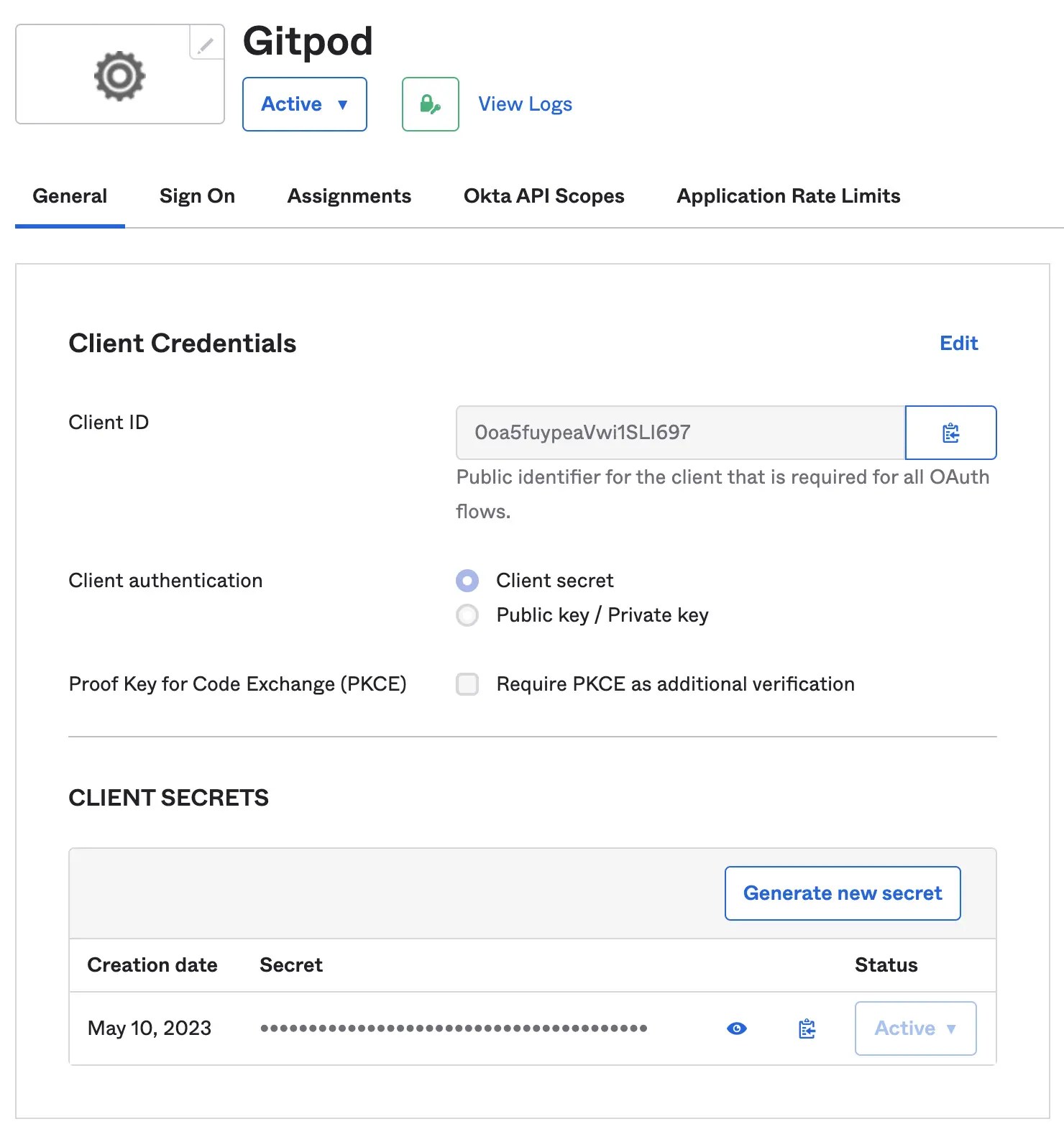
Obtain Client ID & Client Secret
- Copy the
Client IDand use it as input in Gitpod setup (see details above under “General instructions”) - Copy
Client Secretand use it as input in Gitpod setup (see details above under “General instructions”) - Set the
Issuerto your Okta instance, eg:https://amazingco.okta.com/

- Copy the
Continue with Gitpod SSO Configuration verification: Clicking “Verify SSO Configuration”
As prerequisites you will need the following:
- Access to setup a new API Credentials in your GCP Account
Creating a Gitpod SSO Integration
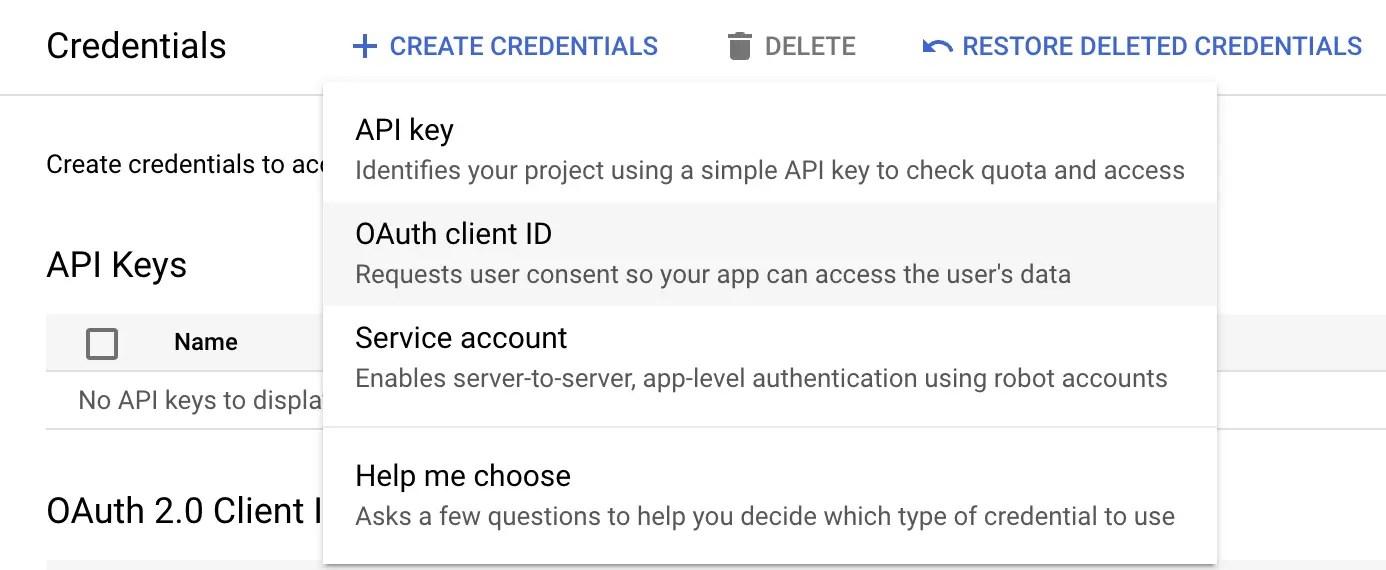
Navigate to your Google Cloud Console, API Credentials
Select Create Credentials, and choose OAuth client ID

Configure your OAuth Client ID, by specifying the Authorized Redirect URIs: Once you’ve created your Identity Provider configuration, you should copy…
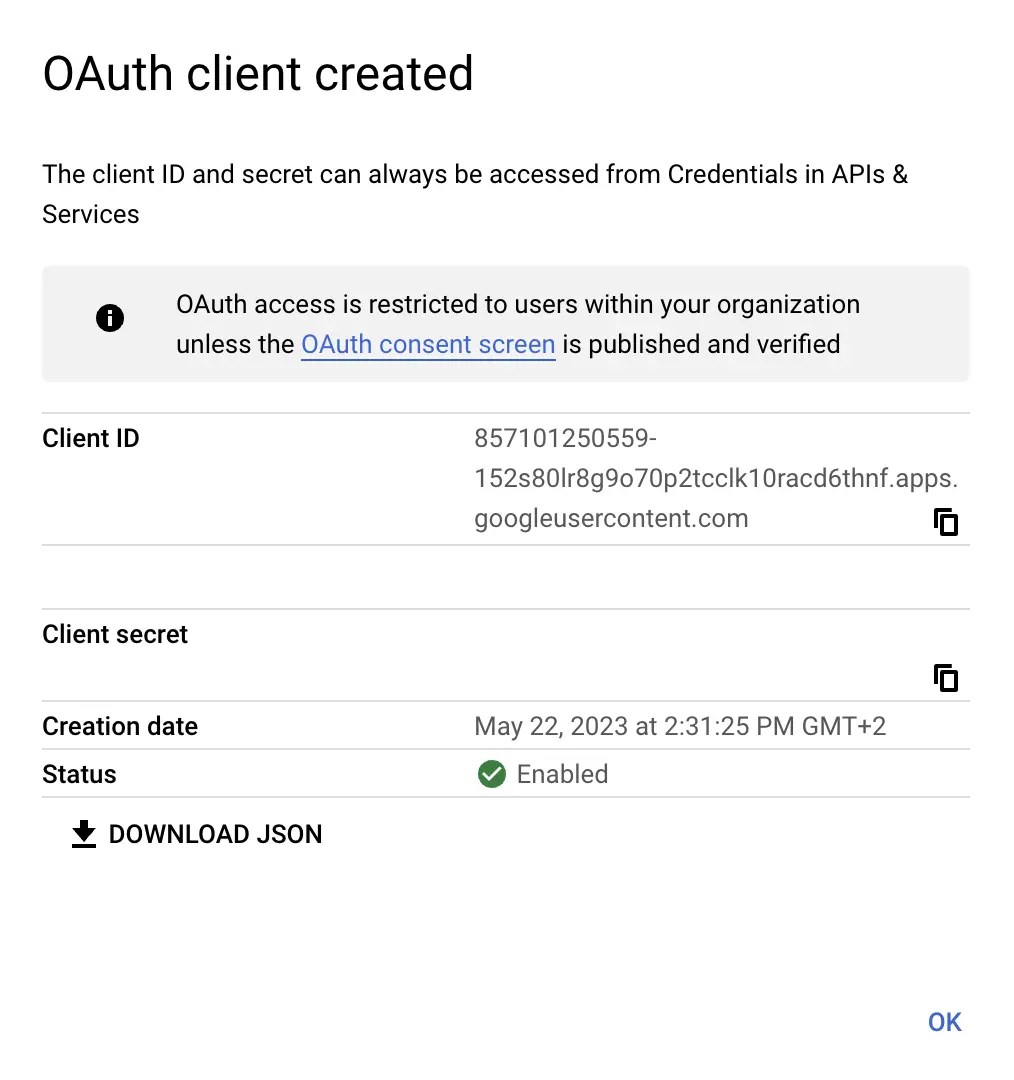
Obtain the Client ID & Client Secret and input these into your Gitpod Setup page

Set Provider’s Issuer URL to
https://accounts.google.comProceed to verify the integration on the Gitpod setup page: Clicking “Verify SSO Configuration”
Azure AD
As prerequisites you will need the following:
- Access to Azure Directory, to Register an Application
Creating a Gitpod SSO Integration
Navigate to your Azure portal > App Registrations
Select New Registration

Name your application - e.g. Gitpod
Select supported account types depending on your organizational needs. Most likely you want Accounts in this organizational directory only
Copy the redirect URL from the Gitpod SSO setup page and set it as the Redirect URI, selecting Web as the application type

From the App Registration Overview, you should obtain the Application (client) ID and copy it into your Gitpod SSO setup page
Create a client secret - navigate to Certificates & Secrets, click New client secret

Name the secret, and set expiry according to your needs.
📌 Once the client secret expires, you (nor anyone else in your organization) will be able to log in to Gitpod. You will need to update the SSO configuration (secret) to continue using SSO.
Obtain the Secret Value and copy into into the Gitpod SSO Client Secret input field
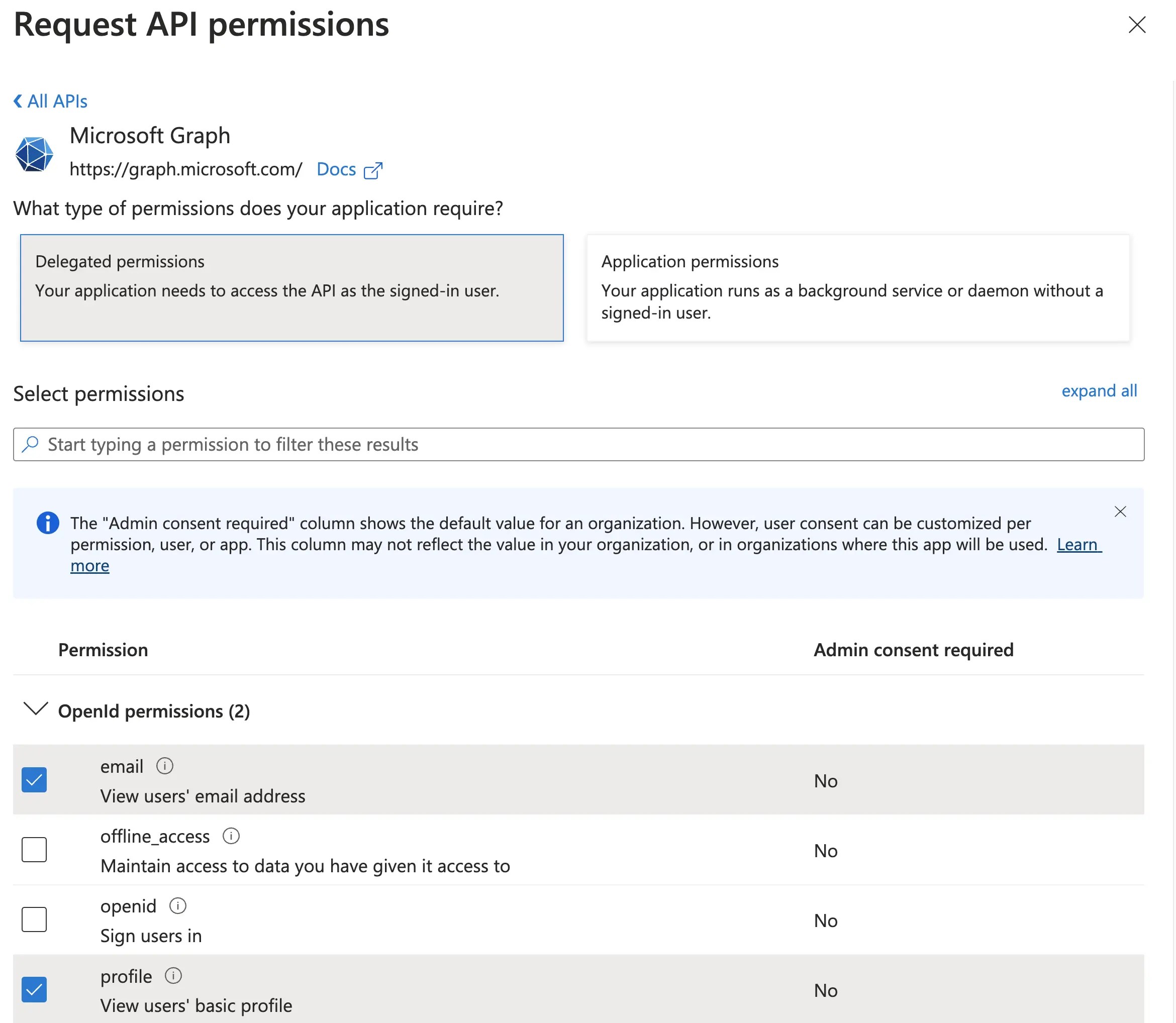
Grant the application access to OpenId
email,openidandprofileinformation- Navigate to API Permissions
- Select Microsoft Graph
- Enable
OpenId.email,OpenId.openidandOpenid.profile
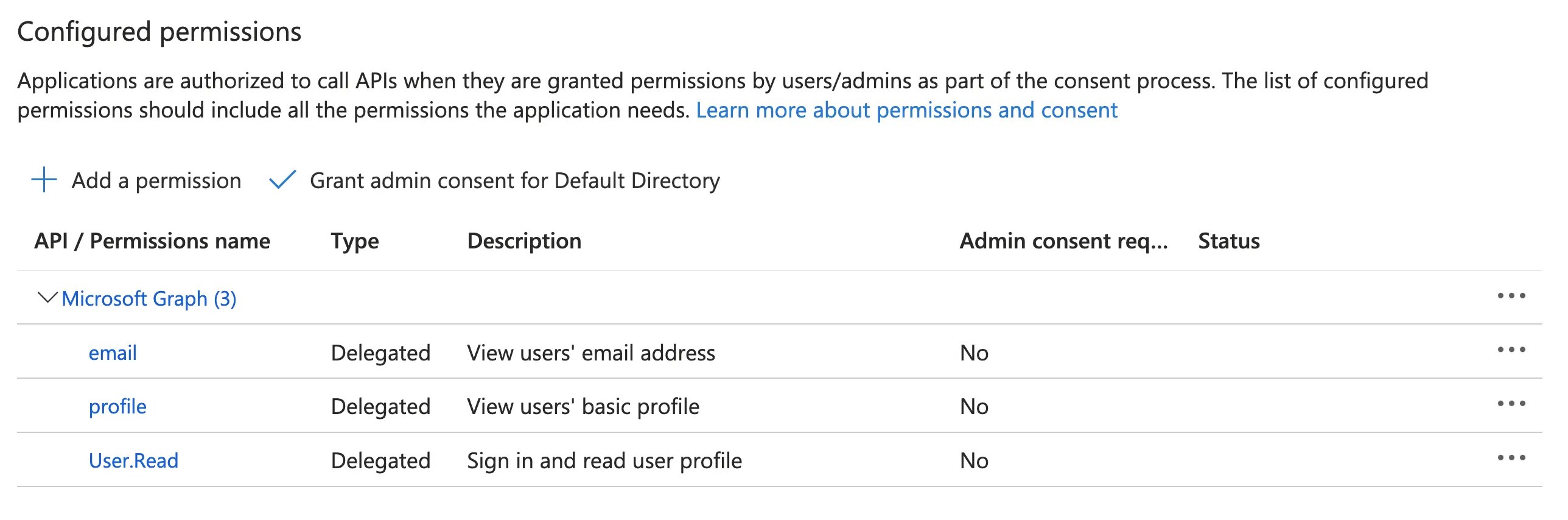
- Once saved, your configured permissions should look as follows:

Obtain the Provider URL
- Navigate to your App Registration > Overview
- Click endpoints

- Find the entry for
OpenID Connect metadata document - Use the URL before the
.well-known/openid-configurationsegment,- For example:
https://login.microsoftonline.com/512571ea-9fc5-494e-a300-625b33c8efa6/v2.0/
- For example:
Proceed to Verify the SSO configuration on the Github SSO setup page: : Clicking “Verify SSO Configuration”
AWS Cognito
Choose this option if you already use AWS Cognito. AWS Cognito is also a good option in a testing or Proof of Value (PoV) scenario where you don’t have an IDP you can easily integrate with. In this scenario, most settings should be left at their defaults.
Follow the Cognito User Pool setup process, then copy the necessary values into the Gitpod SSO Configuration UI
- Navigate to the Cognito page in the AWS console. Select create user pool:

- Configure sign-in experience:

- Select
Cognito user poolas provider type - Select email as the Cognito user pool signin option
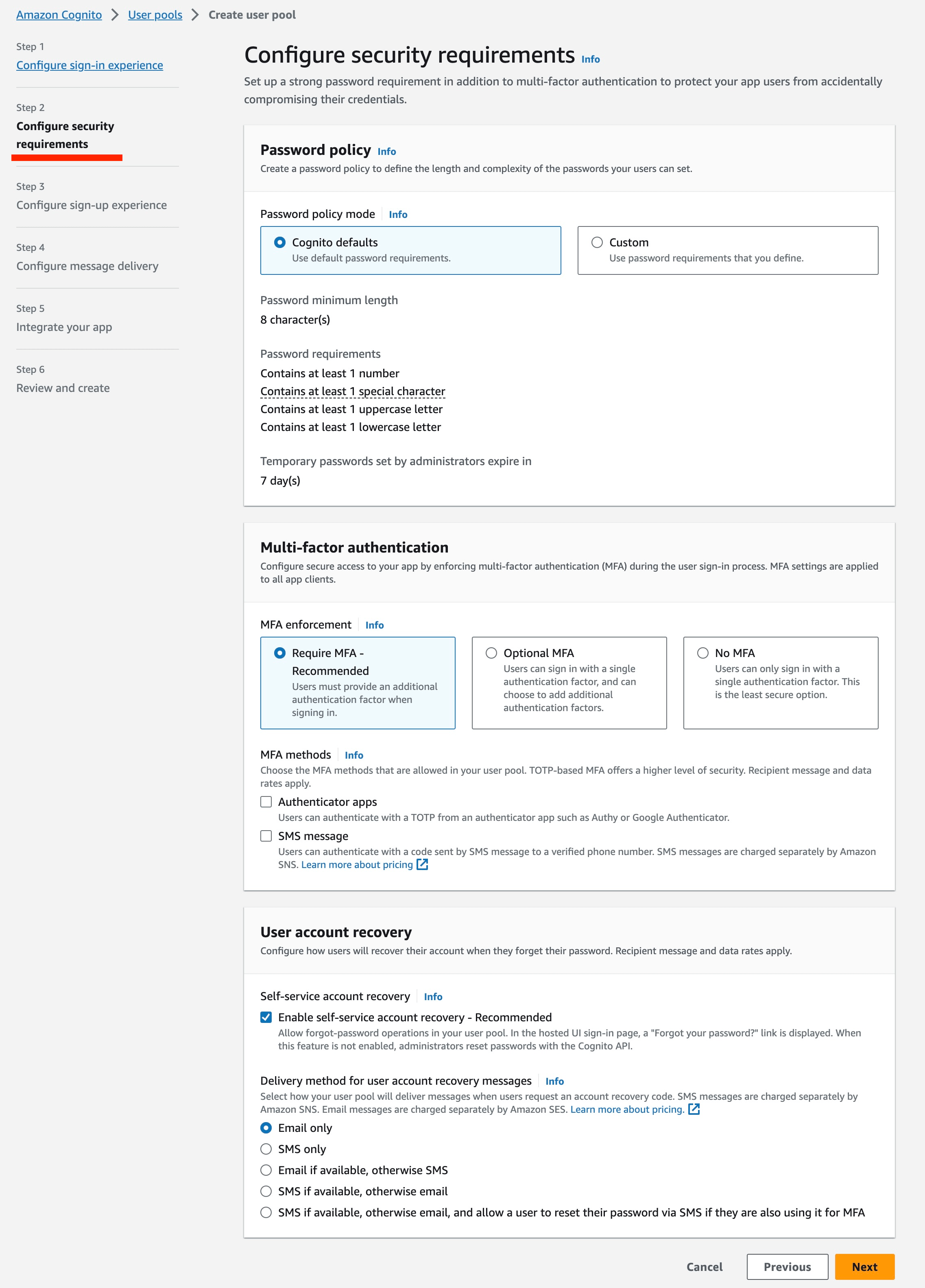
- Configure Security requirements:

- For development purposes, consider modifying the MFA enforcment policy to not require MFA. For all production use cases, configure the MFA and user account recovery sections according to organizational guidelines
- Configure sign-up experience:

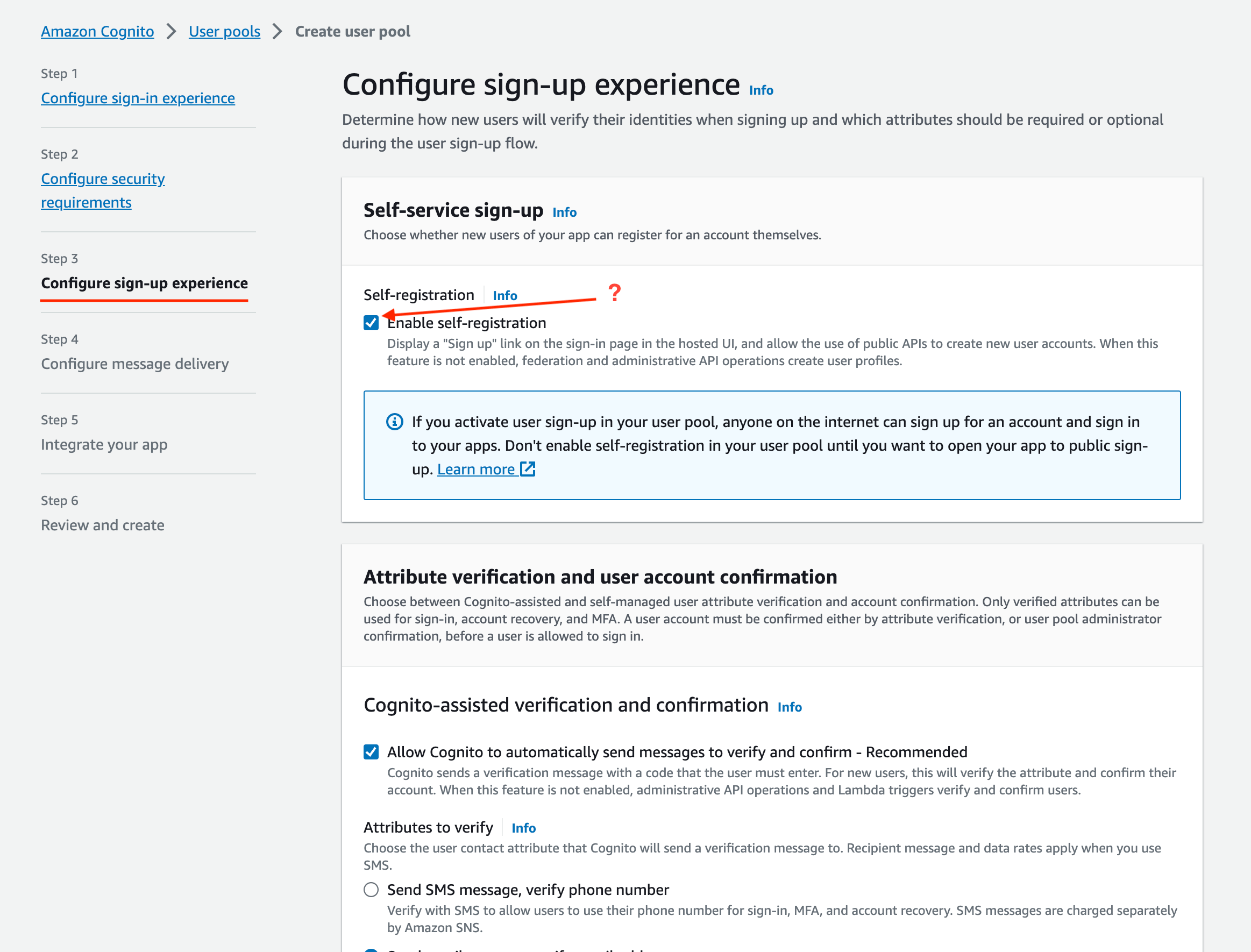
- Disable Self Registration if you want to limit access. For example, if your instance is accessible on the public internet, you may not want anyone to be able to self-register.::WARN> In the
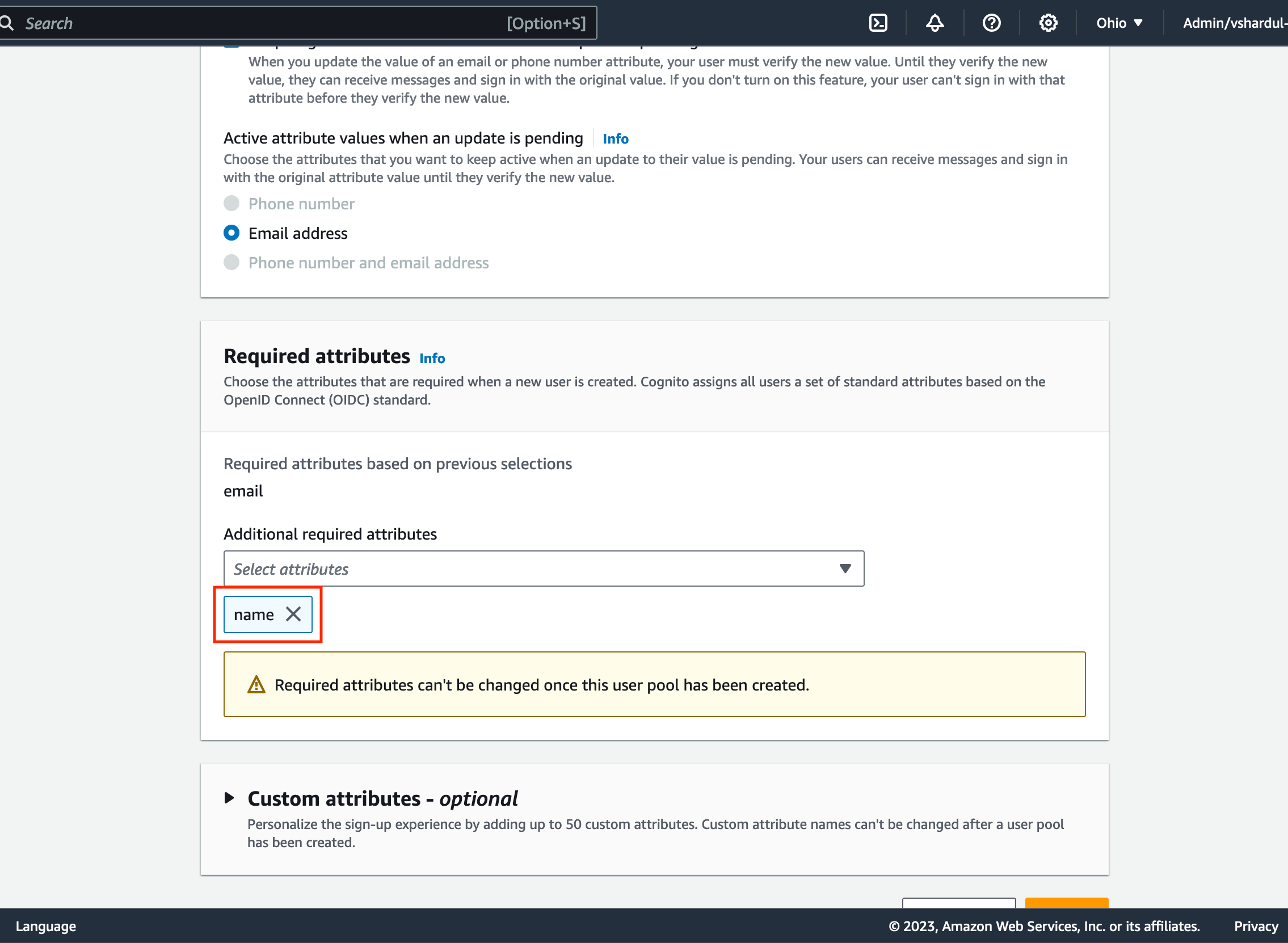
Required Attributessection, ensure that name is selected:
- Disable Self Registration if you want to limit access. For example, if your instance is accessible on the public internet, you may not want anyone to be able to self-register.::WARN> In the
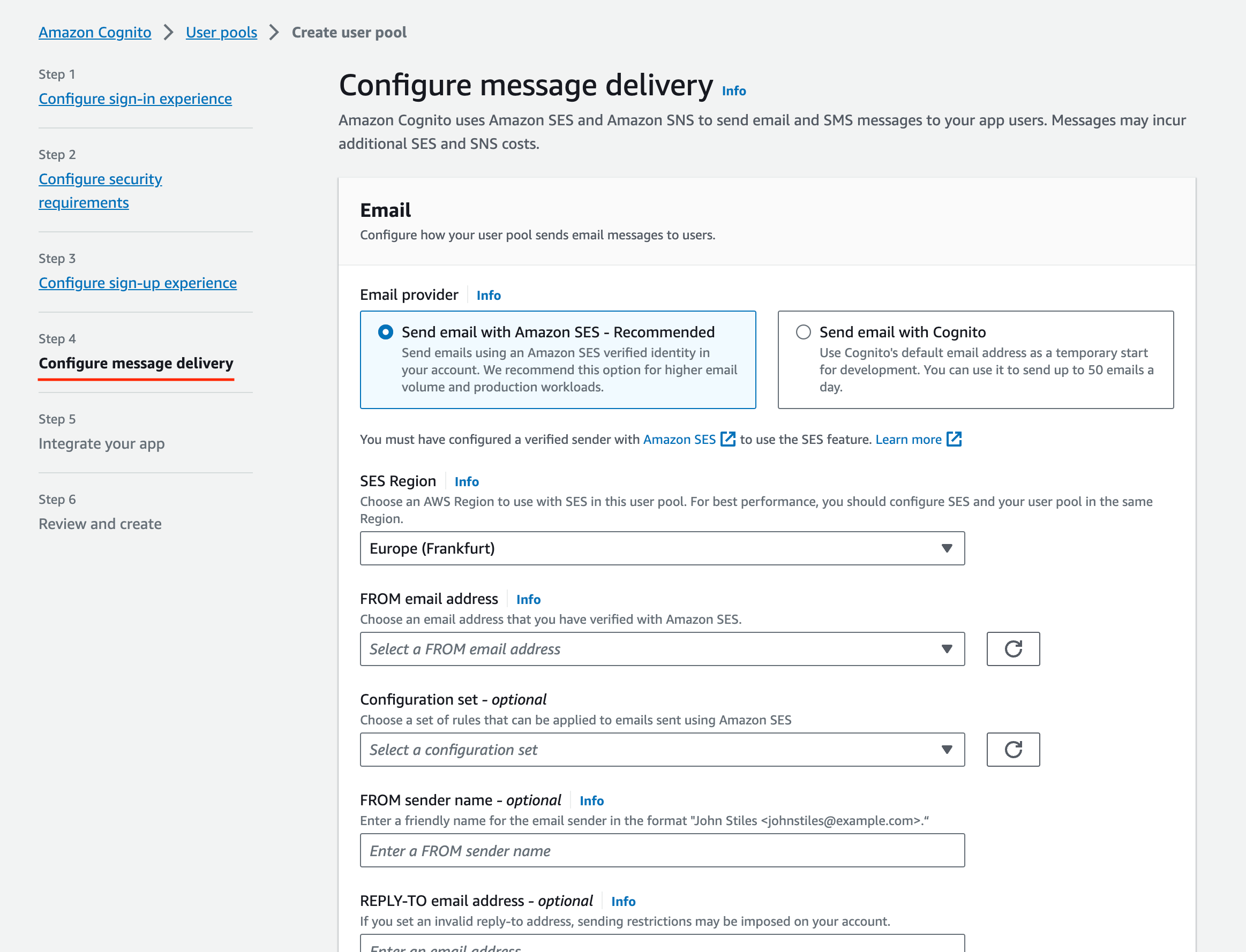
- Configure Message Delivery:

- For dev Setups, use Cognito as the email provider; for production setups, use company SES setup
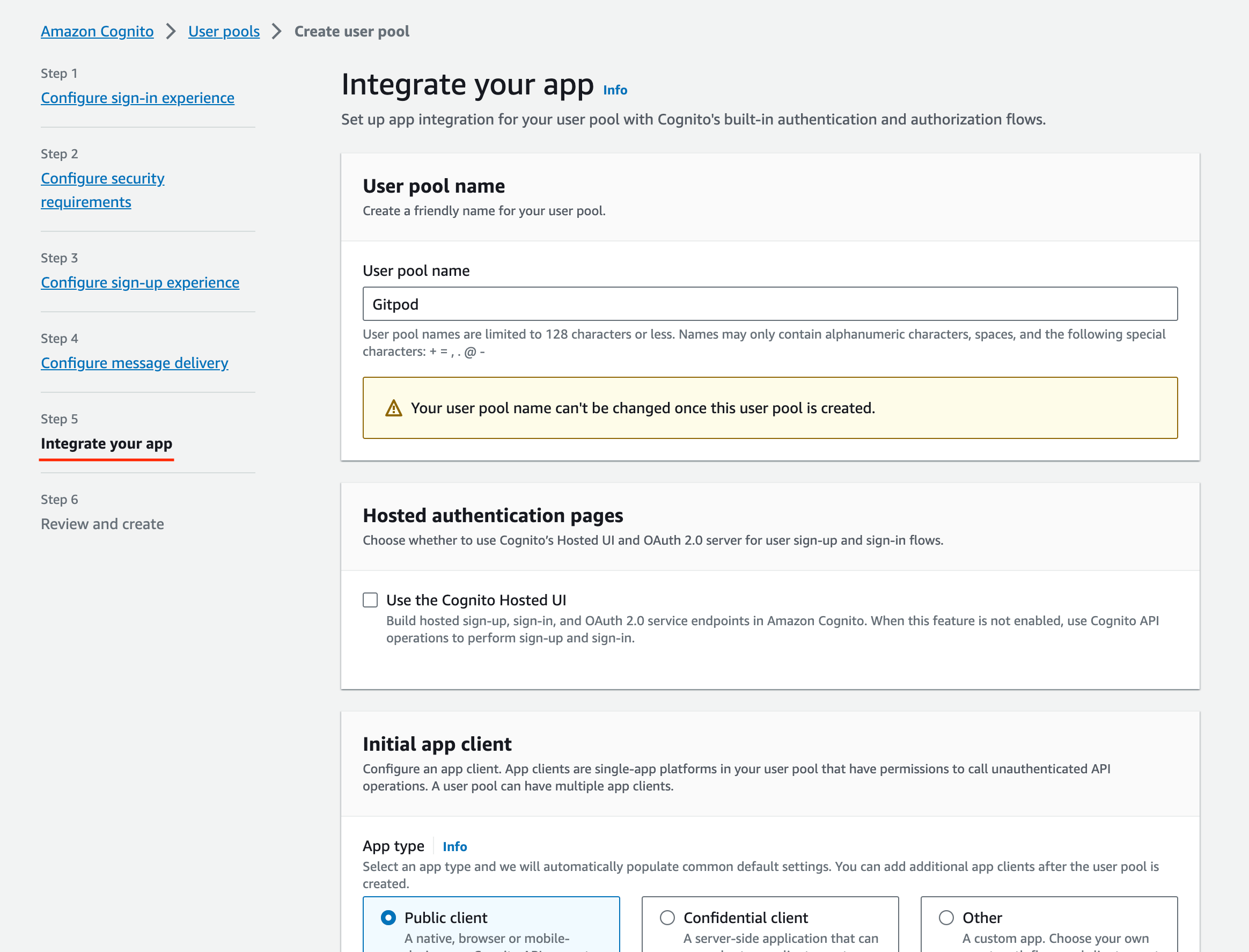
- Integrate your app:

- Follow company best practice for most settings
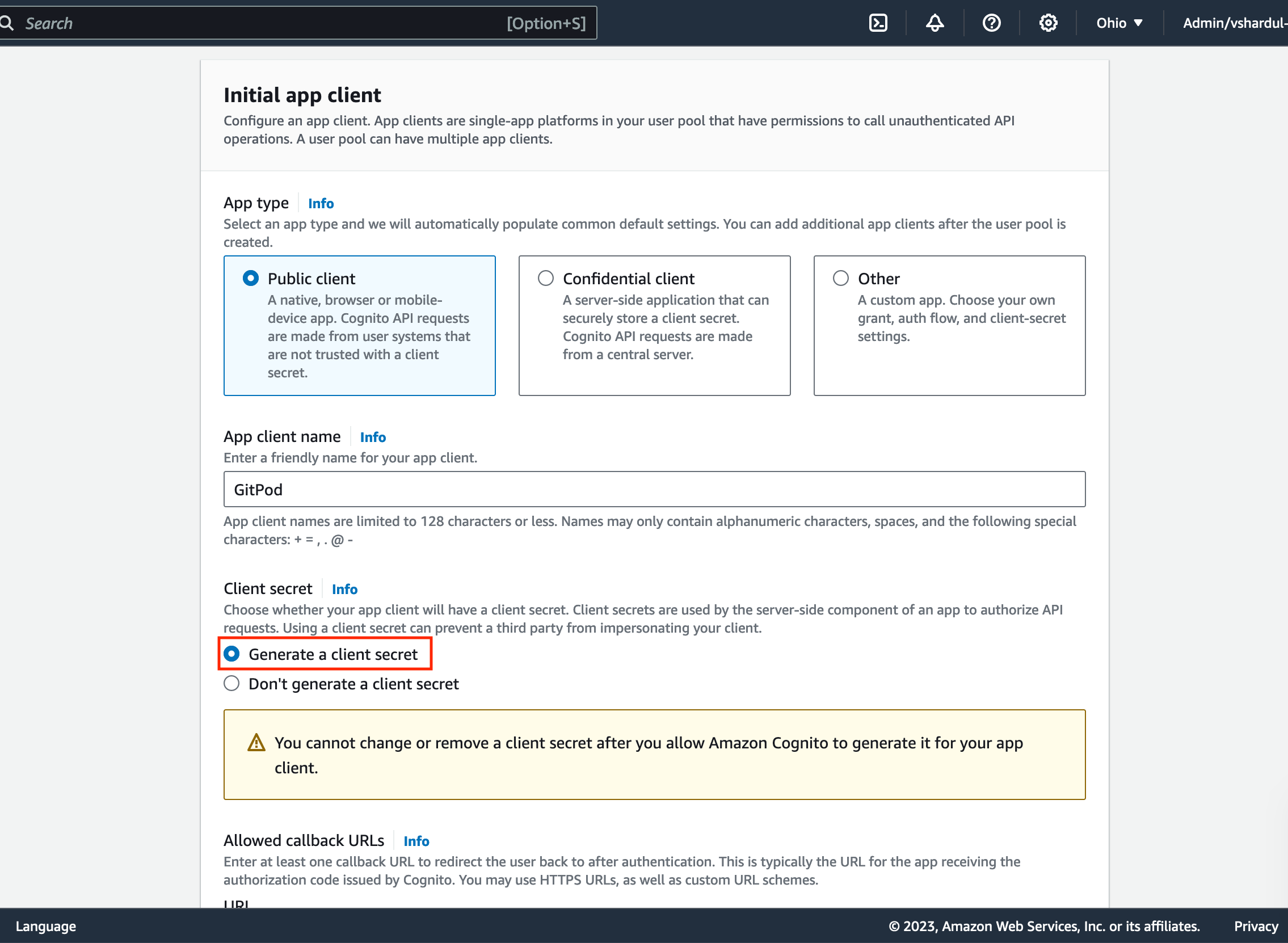
- Ensure to select
Generate a client secretin the Client secret section:
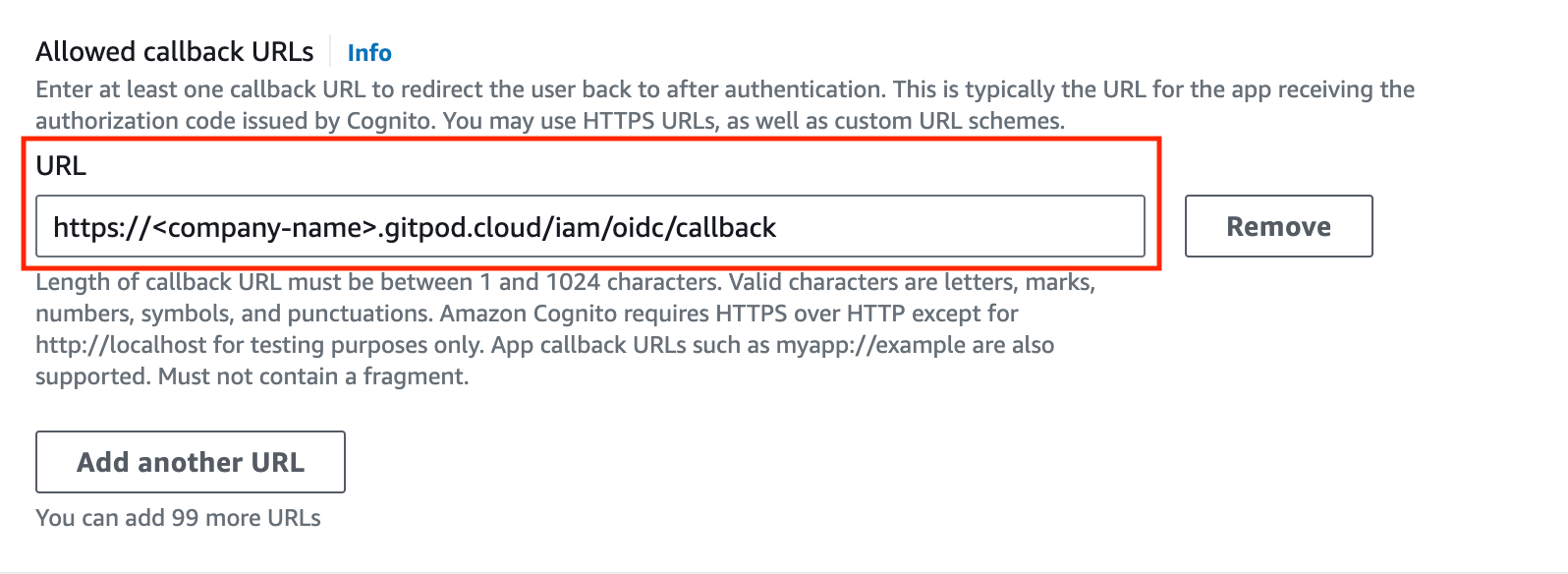
- Define the call back url as provided by the Enterprise instance in the Configure single sign-on setup page (see above):

- As the identity provider, select
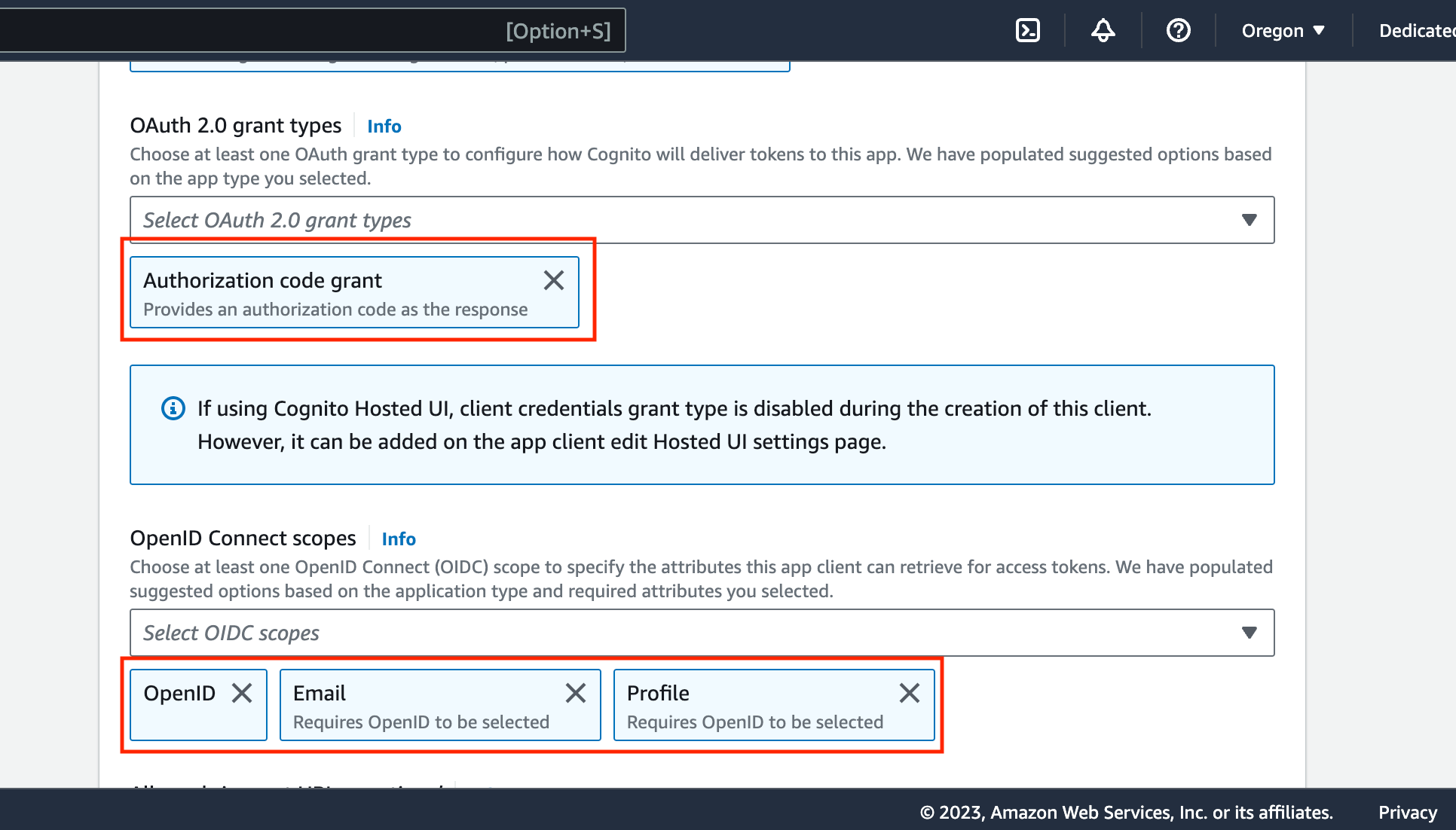
Cognito(under Advanced app client settings) - OAuth 2.0 grant types, select
Auth Code Grant - Under OpenID Connect Scopes, select
OpenID,Email,Profile:
- Now create the cognito user pool. The review page should look similar to this:
- Start pasting the necessary values into the Gitpod SSO setup page. Navigate to:
text
https://cognito-idp.<insert_region>.amazonaws.com/<insert_user_pool_id>/.well-known/openid-configurationThis will return a web page with raw json data: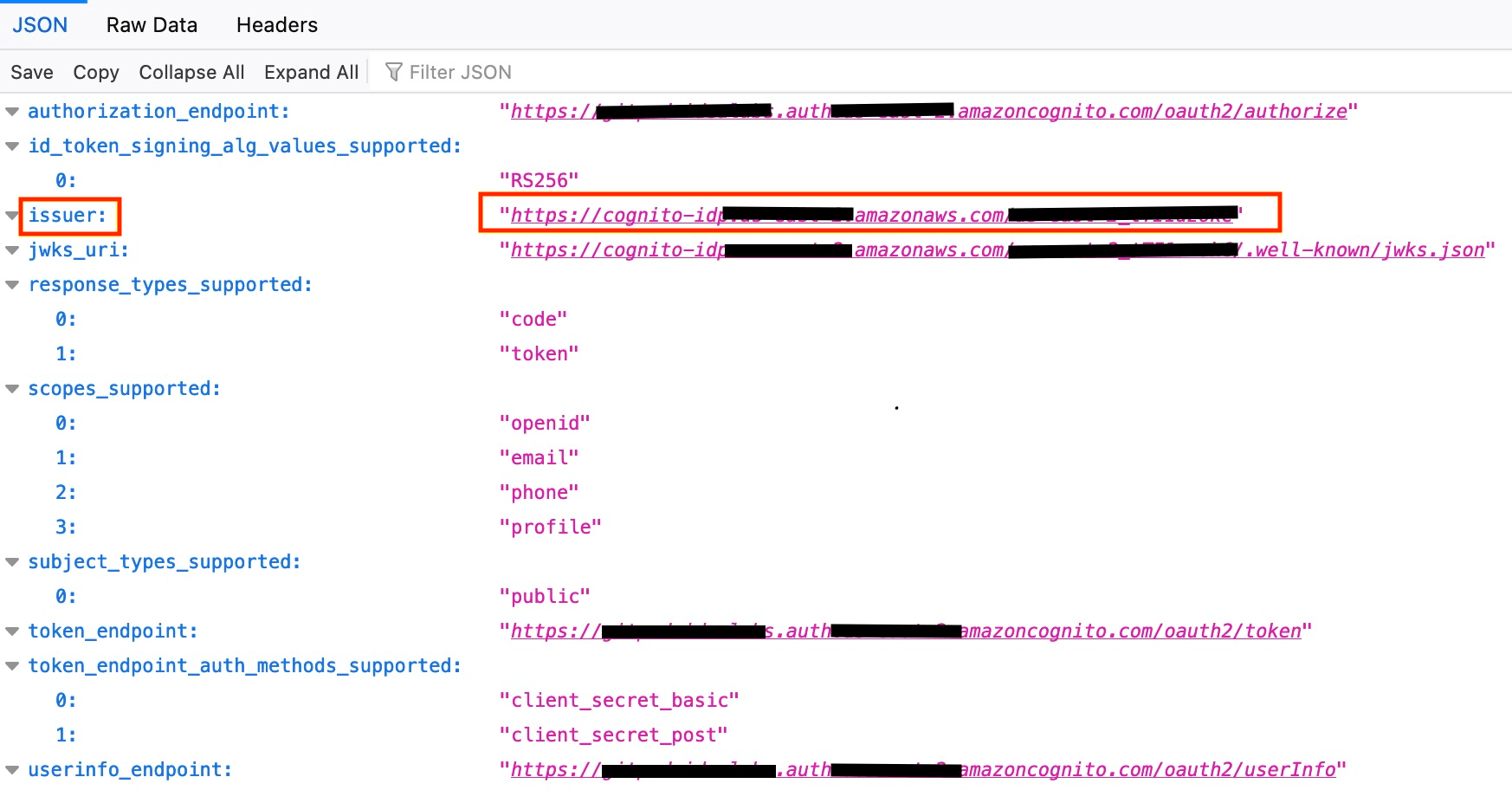
- Copy the
issuer URLhighlighted above into the respective field on the Gitpod SSO setup page
- Navigate to the Cognito console, and find the User pool created above. Navigate to the App client meta data as below:

- Copy the
Client IDfrom the Cognito app client page into the respective field on the Gitpod SSO setup page - Copy the
Client Secretinto the respective field on the Gitpod SSO setup page
- Proceed to Verify the SSO configuration on the Github SSO setup page by clicking “Verify SSO Configuration”